Kerberos Configuration in the Enterprise
Before using Kerberos with Actian X, Kerberos should be appropriately configured in your enterprise.
A primary component of Kerberos is the Key Distribution Center (KDC). The KDC is a server process that performs the core authentication. The authentication protocol is a set of encrypted tickets that are passed from the KDC to client processes or intermediate agents known as “service principals.” For the sake of simplicity, let us assume that a single KDC will perform the Kerberos authentication.
If the enterprise contains only one DBMS Server, a possible option is to execute the KDC on the same machine as the DBMS Server:
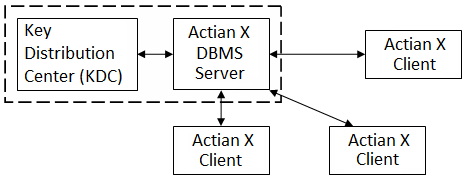
If enough resources are available, it is desirable to install the KDC on a network node separate from the Actian X installation. In this way, security restrictions can be imposed on the Kerberos node that may not be possible if Kerberos resided on the same machine as a DBMS Server:
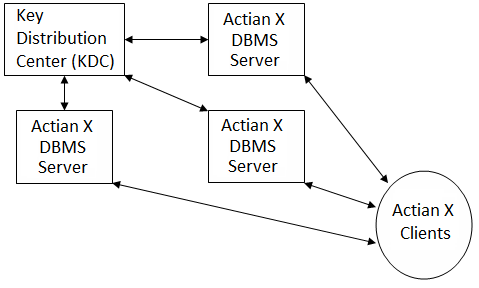
The example above demonstrates why Kerberos is sometimes referred to as “distributed authentication.” The KDC performs authentication for all Actian X nodes in the enterprise, even though the KDC itself resides on a separate network node.
Note: The above example assumes all the Actian X nodes will use Kerberos for authentication, but this is not a requirement; some nodes may continue to use INGRES or SYSTEM authentication.
Last modified date: 04/03/2024