Start the Vector Command Line Interface
The Vector Command Line Interface (CLI) is installed with the Vector instance. It enables you to interact with Vector databases and tables using line-based text commands.
To access the CLI in the Vector instance, you will need to use an SSH (Secure Shell) utility such as PuTTY on Windows or the native SSH client on Linux or Mac OS X. Follow the appropriate procedure below.
To connect to the Vector instance using PuTTY on Windows
1. Start the PuTTY telnet client on your machine.
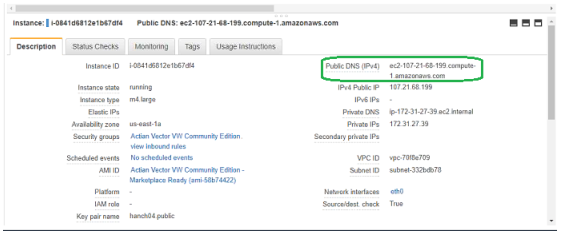
2. From the Description tab of the Vector EC2 instance browser window, copy the Public DNS to the Clipboard:
3. On the PuTTY Session page, paste the DNS into the Host Name (or IP address) field.
4. On the Connection, SSH, Auth page, browse for and load your local private key file (.ppk) used for authorization.
5. Click Open to start your terminal session.
The “login as” prompt is displayed in the terminal session window. Use actian for the login.
To connect to the Vector instance using SSH on Linux or OS X
1. In a command-line shell, change directories to the location of the private key file that you created when you launched the instance.
2. Ensure that the private key file (.pem) has the appropriate file permissions (400). If not, use the chmod command to ensure that the permissions are set correctly:
chmod 400 /path/my-key-pair.pem
3. Use the ssh command to connect to the instance. Specify the private key (.pem) file and actian@public_dns_name. For example:
ssh -i my-key-pair.pem actian@ec2-198-51-100-1.compute-1.amazonaws.com
You receive a response such as the following:
The authenticity of host 'ec2-198-51-100-1.compute-1.amazonaws.com (10.254.142.33)'
can't be established.
RSA key fingerprint is 1f:51:ae:28:bf:89:e9:d8:1f:25:5d:37:2d:7d:b8:ca:9f:f5:f1:6f.
Are you sure you want to continue connecting (yes/no)?