License Administration
The following topics discuss Zen license models and working with license keys:
License Administration Concepts
This section discusses the following topics:
License Models
Zen products offer two license models: concurrent user and capacity-based. The concurrent user model counts users, while the capacity-based model measures the data in use. In both models, once a set limit is reached, whether users or data, no additional database activity is allowed. For the user count model, no new users can access any data. For the data capacity model, no new data access requests are accepted. Once user count or data usage fall below the limit, new activity is allowed.
Concurrent User License Model
With the concurrent user license model, each product key specifies a licensed user count. A user count allows the specified number of concurrent connections to the Zen database engine. Users are counted by network address. The IP address is used for TCP/IP.
Each computer that accesses the Zen as a client session counts as one user. Multiple applications on a single client computer are counted as one user, not separate users. Internally, Zen assigns each machine a serial number and counts all connections with the same serial number as coming from one machine. A machine with multiple NICs, for example, is recognized as one machine. Each Terminal Server session also counts as one user.
Collectively, all applications that access the database engine using the same network protocol and address and running on the same machine as the engine are counted as one user.
A user is counted for each unique incoming protocol from the same client computer session. If different address formats of the same protocol are used, only one user is counted. For example, if one application uses IPv4 and another uses IPv6, only one user is counted if both applications run on the same machine. IPv4 and IPv6 are just different address formats of TCP/IP.
Obtaining a User Count
An initial user count is provided as part of the product key. This product key is issued by Actian Corporation or by your application vendor if the Zen database engine is embedded in an application.
You may also increase the user count beyond the initial amount provided by the product key. See Increasing User Count.
Capacity-based License Model
The capacity model shifts the emphasis from how many users to how much work the database server performs. The model is based on the process capacity of the engine determined by the amount of data in use. This amount is the total size of data files authorized to be opened concurrently.
Data in Use
Data in use is defined as the total size of all concurrently open data files. A data file is a file created by an application to provide the data processed by that application. Data in use limit is the maximum permitted amount of all concurrently open data files as granted by a license agreement.
The value for data in use increases when a data file is first opened. Subsequent opens to an already open data file do not add to the total. Data in use also increases if an open file increases in size. Operations on an already open file continue to be permitted even if the size of the open file increases beyond the data in use limit.
The value for data in use decreases when a data file is closed by the final user to have the file open. Since more than one user can access the same data file, all opens must be closed before data in use decreases.
Messages pertaining to data in use are logged to the various Zen logging repositories. See Message Logging.
The database engine uses various files for its own internal processes, such as Zen system files, metadata files, dbnames.cfg, and default databases. Files used for internal processes do not increase the value for data in use.
Estimating Data in Use
You can determine what size license you need for your business based on information about your data usage. Zen provides Capacity Usage Viewer to provide that information.
Capacity Usage Viewer is a tool that records peak daily data use. It renders those figures into a graph that displays your use over time. Capacity Usage Viewer enables you to select time periods ranging from All to Last week. You can also zoom in to view the data for a customized time period.
To estimate your capacity requirements, select a time period that includes maximum and minimum licensing requirements. For example, if your business has quarterly cycles, include at least 90 days worth of data. By reviewing data usage over time, you can ensure that the license capacity meets or exceeds your peak usage requirements.
Capacity Usage Viewer is covered in more detail elsewhere in the user documentation.
Note: The Monitor tool can also help you estimate session count and data in use.
Behavior When Data Use Limit Is Reached
The following summarizes the expected behaviors when the limits are reached for data in use.
• The database engine denies requests for new file opens and returns status code 161 to the application. (Status code 161 is returned if the file to be opened exceeds 110% of the data in use limit. A slight buffer above 100% is provided because an increase in data in use can also result from the growth of currently open data files.)
• Subsequent opens to an already open data file are permitted. That is, if a file is already open and data in use reaches or exceeds its limit, other users can still access the open file.
• Note that data in use also increases if an open file increases in size. Operations on an already open file continue to be permitted even if the size of the open file increases beyond the data in use limit.
• The value for data in use decreases when a data file is closed by the final user to have the file open. Since more than one user can access the same data file, all opens must be closed before data in use decreases.
• Messages pertaining to data in use are logged to the various Zen logging repositories. For example, a message first alerts you when data in use reaches 90% of the data in use limit.
Corrective Action When Data in Use Limit Is Reached
The following suggested corrective actions may be taken when the data in use limit is reached in order to continue working with the engine.
• Authorize an increase key for data in use. An increase key can be authorized at any time and does not require that you close data files or stop the database engine. The increase is immediately available. See Increasing Data in Use Limit
• You may try closing some of the currently open data files. However, this action requires that you know which data files are safe to close without resulting in incorrect data, incomplete records or aborted transactions
Obtaining an Initial Data in Use Limit
Initial data in use limits are provided in the product key. The key is issued by Actian Corporation or by your application vendor if the Zen database engine is embedded in an application.
You may also increase the data in use beyond the initial amount provided by the product key. See Increasing Data in Use Limit.
License Enforcement
Licensing for Zen is enforced by use of product keys, which you manage using License Administrator. This tool allows you to authorize and deauthorize keys and view license information. It has both a graphical and command line interface. You authorize a key for one of two purposes:
Authorize a Product
Product authorization is a key validation process that associates certain machine information with the license for a product, called the "product key." This association results in a unique installation identification that ensures the copy of software is legitimate and on the appropriate machine.
When you authorize a product key, the unique installation ID is sent to Actian Corporation to verify the authenticity of the key and ensure it is not being used for multiple installations. This process authorizes the product for use. When the product key is authorized or deauthorized, your remaining authorizations are displayed.
Note that after you have authorized a product key on a machine, certain changes to the machine can disable the key. If you need to make changes to the machine, deauthorize the key first. Doing so disassociates the product key from its unique installation ID. After you complete the hardware configuration changes, you can again authorize the product key.
Authorization Access Through a Proxy Server
If you are using a proxy server to reach the Zen license service, you must configure it to allow product authorization. You can configure the proxy server before you install Zen or you can skip product authorization during installation, then configure the proxy server, and then authorize.
This topic covers the following items:
Windows Proxy Servers
We recommend that you use a browser to configure proxy servers. If you are unable to use a browser, then you can use the steps given here. These steps involve editing the Windows Registry.
In a 64-bit Windows operating system, two keys in the Registry can store proxy server settings:
• HKEY_LOCAL_MACHINE\Software\Actian\Zen\ELS
• HKEY_LOCAL_MACHINE\Software\Wow6432Node\Actian\Zen\ELS
Depending on the Zen edition (Enterprise Server, Client, Cloud Server, or Workgroup), the ELS proxy server settings can be created in either location. Licensing manager looks for its proxy server settings first in the HKEY_LOCAL_MACHINE\Software\Wow6432Node\Actian\Zen\ELS\ key. If it cannot locate them there, then it looks in the HKEY_LOCAL_MACHINE\Software\Actian\Zen\ELS\ key.
If you are editing Registry settings for proxy servers, you first need to find the correct location.
1. Begin by looking for a Wow6432Node. If it exists, edit the proxy server Registry settings in the Actian\Zen\ELS\ key.
2. If you find no Wow6432Node, move to the Software directory and edit the proxy server Registry settings in the Actian\Zen\ELS\ key.
3. Modify the Windows Registry by adding the following to the Actian\Zen\ELS\ key:
Key | Value |
|---|---|
String Value | proxy_host |
DWORD Value | proxy_port |
String Value | proxy_userid |
String Value | proxy_passwd |
Note: The proxy_host and proxy_port values are the only ones required by Zen. Depending on the configuration of your proxy server, you may also need to add proxy_userid and proxy_passwd. | |
4. Authorize Zen using License Administrator. See To Authorize a Key for the GUI and To Authorize a Key for the CLI.
Caution! Editing the Registry is an advanced procedure. Improper edits can cause your operating system to fail to start or behave incorrectly. If necessary, obtain the services of a qualified technician to do the editing. Actian Corporation does not accept responsibility for a damaged registry.
Linux and macOS Proxy Servers
On Linux and macOS systems, to configure a proxy server to allow license authorization you must use the psregedit utility to modify the Zen registry. Zen does not support any other method of authorization through a Linux or macOS proxy server. Use psregedit to add registry values for the following key names:
• proxy_host
• proxy_port
• proxy_userid
• proxy_passwd
The proxy_host and proxy_port values are the only ones required by Zen. Depending on the configuration of your proxy server, you may also need to add proxy_userid and proxy_passwd.
The following example shows a command to set the proxy_host registry value:
psregedit -set -key PS_HKEY_CONFIG\SOFTWARE\Actian\Zen\ELS -value proxy_host -type PS_REG_STR "192.168.220.128"
After modifying the Zen registry, you can then authorize Cloud Server using the License Administrator CLI tool. See To Authorize a Key. If you decide to stop using the proxy, use psregedit -delete to remove the values for proxy_host and proxy_port.
Note: In the past, users could enter these values in the els.ini file. However, as of Zen v15 SP1, use of this file is deprecated on Linux and macOS.
Offline Authorization Without Internet Access
If you install Zen on a system without Internet access, you may authorize the product key using offline authorization. Offline authorization involves three tasks:
1. On the machine without internet connectivity, generate an Authorization Request Data file. This file has the extension .ath.
2. Upload the file to an authorization server from a machine with internet access. In response, an Authorization Key Data file is downloaded in the form of a product key file. This file has the extension .pky.
3. Place the .pky file on the machine without Internet connectivity to authorize Zen.
The quickest and simplest method for authorizing Zen is using online or remote authorization. Whenever possible, try to authorize your Zen product using one of these methods. The Zen installation, for example, allows you to authorize online as part of the installation process.
Key Status, or State
The status of a product key is displayed in License Administrator as its state. Key states include these:
• Active – Key is authorized and available for use.
• Inactive – Key is no longer in use. This state is reserved for situations where the key is incompatible with the current engine. Examples would include previous versions of Zen, such as v10 and earlier on v11, or a Workgroup key on a server engine, or 32-bit key on a 64-bit engine.
• Expired – Key is no longer available for use. Temporary keys move to the Expired state once their evaluation period has passed.
• Disabled – Key is no longer available for use. If a key is disabled because of a failed validation, it can be restored to active by fixing the problem and then performing a validation on the key.
• Failed Validation – Key is usable but only for a set number of days. See Failed Validation and Failed-Validation Period.
Failed Validation and Failed-Validation Period
If a key fails validation, you have a set number of days to remedy any condition that caused it to fail. This period of time, referred to as the "failed-validation period," is reported in the Expiration Date column of License Administrator, as shown in GUI Visual Reference. If the condition for the failed validation is not corrected by the date, the key changes state to disabled.
After you implement changes to correct the failed validation, perform a Validation action. See To Perform a Validation. The validation, among other actions, verifies the current machine signature and key combination. If the conditions were corrected, the state of the key changes to active.
More than one condition at a time can cause a failed validation. You can correct what you think is the sole condition, yet the key remains in the failed validation state. If so, see the zen.log file for more information. That log file contains all of the conditions causing the failed validation. See Zen Event Log (zen.log) in Advanced Operations Guide.
If the changes that caused the failed validation are due to intentional hardware upgrades performed without first deauthorizing the key, the next step is to repair the key.
Repairing a Disabled or Failed Key
License Administrator provides the functionality to perform a repair on a key that is disabled or has failed validation. Moreover, it not only repairs the key, it automatically deauthorizes the key and then authorizes it again on the same machine.
You can perform a repair using either the graphical user interface (see License Administrator Graphical User Interface) or the command line interface (see License Administrator Command Line Interface).
If the problem is more significant than a change in hardware, for example, the machine on which a key is installed no longer boots, you cannot repair the key. In that case, contact support for assistance.
Increase User Count or Data in Use
Situations can arise in which you want to increase user count or data in use from the initial amount provided by the permanent product key. You increase the amount by authorizing an increase key. Multiple increase keys can be authorized on a product key.
When you authorize the key, the increase is available immediately. You do not need to restart the database engine.
To authorize an increase key, you must already have a permanent product key present on the system. The software vendor ID number for an increase key must match the vendor ID number for an installed permanent key. Increase keys obtained from Actian Corporation are universal. That is, they are compatible with any permanent key from any vendor.
Increasing User Count
You increase the user count by authorizing a user count increase (UCI) key. See To Authorize a Key and To Determine a Total User Count. UCI keys are provided by Actian Corporation or an application vendor.
If you deauthorize a permanent product key, all user count increase keys associated with that permanent key are also deauthorized. If you deauthorize a UCI key, only the user count increase associated with that UCI key is deauthorized.
Trial versions of the software include a trial license that have a set user count that cannot be increased.
Increasing Data in Use Limit
Actian Corporation or an application vendor offers a key to increase the data in use limit. You immediately increase the value of the data in use limit when you authorize the key. A restart of the database engine is not required. A permanent key must be present to authorize an increase key. An increase key cannot be authorized onto a temporary key. See To Authorize a Key and To Determine the Data in Use Limit.
If you deauthorize the permanent product key, all increase keys associated with that permanent key are also deauthorized. If you deauthorize an increase key, only the data in use increase associated with that key is deauthorized.
Note that the database engine logs a message to the Zen logging repositories when the limit for data in use is increased. The message contains the current limit and usage. See also Message Logging. You can monitor the current, peak, and maximum values of data in use with the Monitor utilities. See Monitoring in Advanced Operations Guide.
Trial versions of the software include a trial license that have a set value for data in use that cannot be increased.
Message Logging
Messages pertaining to licensing are logged to the various logging repositories used by Zen, such as Notification Viewer. See Reviewing Message Logs in Advanced Operations Guide.
License Administrator Graphical User Interface
The graphical user interface (GUI) License Administrator runs only on Windows platforms and allows you to authorize and deauthorize keys, increase user count and data in use limits, monitor session counts, and view license information. You can start the GUI as a stand-alone application or from within Zen Control Center (ZenCC). You can administer licenses for local or remote database engines with the GUI.
See also GUI Tasks for the tasks specific to the graphical user interface.
GUI Visual Reference
The following illustration shows the GUI. The table below the image describes the GUI objects. Click an area of the image for which you want more information.
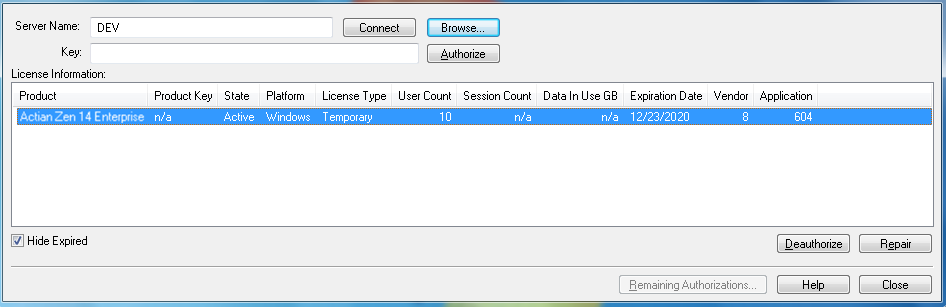
GUI Object | Description | Related Information |
|---|---|---|
Server Name | By default, shows the name of the server that the License Administrator is accessing. This object is also an entry field into which you can type the name of a server. If you have typed in a server name but not clicked Connect (or pressed Enter), the field can contain a server name that differs from the one in the title bar. The title bar always shows the server that License Administrator is accessing. The Server Name field can also be populated if you click Browse and choose a server. | |
Connect | Establishes communication between License Administrator and the computer listed in the Server Name field. | |
Browse | Allows you to choose a server on which to administer licenses. | |
Key | Accepts a key (a combination of letters and numbers) typed in or pasted. | |
Authorize | Authorizes the key entered in the Key field on the specified database engine. The Server Name field shows the server on which the database engine is running. This button is enabled if the key in the Key field is valid and a database engine is running on the specified computer. | |
License Information | Lists the license information for the specified computer: • Product – The name of the Zen product, such as Enterprise Server, Cloud Server, or Workgroup. • Product Key – The Product Key number associated with the corresponding product license. • State – The status of the Product Key. Values are Active, Inactive, Expired, Disabled and Failed Validation. (A license can be disabled if certain hardware configuration items have changed since the key was applied.) • Platform – The combination of Zen product, operating system, and bit architecture to which the license applies. • License Type – The type of license, such as permanent, temporary or an increase license for user count, session count, or data in use. • User Count – The user count for the specific license. • Session Count – The session count limit for the specific license. • Data In Use GB – The data in use limit in gigabytes for the specific license. • Expiration Date – The date on which a license expires, if applicable, or "n/a" if not applicable. • Vendor – A unique number identifying the vendor software that installed the license. • Application – A unique number identifying the application to which the license applies. | |
Hide Expired | Hides all expired licenses in the list of licenses for the current session of License Administrator. This checkbox is selected by default. | |
Deauthorize | Deauthorizes the selected key from the specified server. If the selected key is a permanent key, also deauthorizes all increase keys (user count, session count, data in use) associated with the permanent key. This button is enabled when a Product name is selected in the License Information list. | |
Repair | Repairs, deauthorizes, and authorizes the selected key on the specified server. This button is enabled when a Product name is selected in the License Information list. | |
Remaining Authorizations | Displays the remaining number of authorizations for all product keys and the remaining number of repairs that a user can perform on a key in a state of Failed Authorization or Disabled. This information also displays automatically at the time of authorization and deauthorization, if applicable. | |
Help | Displays the online help for License Administrator. | |
Close | Closes License Administrator. |
License Administrator Command Line Interface
The command line interface (CLI) runs on all platforms supported by Zen. The CLI is functionally equivalent to the GUI. You can administer licenses for local or remote database engines with the CLI.
The GUI and the CLI list information about the authorized licenses, such as the type of license, user count, session count, data in use limit, platform, expiration date, and so forth. License key information is also available from the installation media.
CLI Syntax
The CLI uses the same syntax on all platforms:
tool_name -option parameters
The tool name is one of the following:
• clilcadm.exe (Windows 32-bit)
• w64clilcadm.exe (Windows 64-bit)
• clilcadm or clilcadm64 (Linux or macOS)
The following table describes the command line options and parameters.
Options and Parameters | Function |
|---|---|
-<interpret | i> key | Lists license information for all keys or for the specified key: • Product – The name of the Zen product, such as Enterprise Server, Cloud Server, or Workgroup. • Product Key – The Product Key associated with the corresponding product license. • State – The status of the Product Key. Values are Active, Inactive, Expired, Disabled and Failed Validation. A license may be disabled if certain hardware configuration items have changed since the key was applied, such as machine name. • Platform – The combination of Zen product, operating system, and bit architecture to which the license applies. • License Type – The type of license, such as permanent, temporary or an increase license for user count, session count, or data in use. • User Count – The user count for the specific license. See also Concurrent User License Model. • Session Count – The session count limit for the specific license. • Data In Use GB – The data in use limit in gigabytes for the specific license. See also Capacity-based License Model. • Expiration Date – The date on which a license expires, if applicable, or "n/a" if not applicable. • Vendor – A unique number identifying the vendor software that installed the license. • Application – A unique number identifying the application to which the license applies. |
-<number | n> [key] | Displays the number of remaining authorizations for the specified key. Note: If no key is specified, remaining authorization information for all product keys is displayed. |
-<authorize | a> <key | authorization_filename.pky> | Authorizes the specified key or authorization key data file (offline authorization). |
-<deauthorize | d> key | Deauthorizes the specified key from the computer where the tool is running. If the key is a permanent key, also deauthorizes all increase keys (user count, session count, data in use) associated with the key. |
-<clear | c> [key] [force] | Clears from the machine all permanent keys and their associated increase keys for user count, session count, or data in use. If a key is specified, only the specific key and its associated increases for user count, session count, or data in use are cleared. If no key is specified, all keys and associated increases are cleared. Note: This command is useful if you are unable to deauthorize a key because of changes in the hardware configuration and you need to authorize another set of keys. You could clear the key(s) and authorize the product with a different key than the one(s) you cleared. If the force option is included, a confirmation message is not displayed. Note: This option only removes a key from the local Zen server. It does not deauthorize the key from the unique machine signature maintained by Actian Corporation. That is, it does not remove the record of the link between the machine signature and the key. |
-<generate | g> key output_filename | Generates authorization request data file for offline authorization. The product key and output filename are both required. |
-<repair | e> key | Repairs and authorizes a key, if repair is possible. Use must meet the following conditions: • The key to be repaired must be compatible with the version of the database engine currently installed. • The key to be repaired must be in a "disabled" or a "failed validation" state. • A permanent key cannot be in the "active" state. • There must be Internet access to communicate with the Zen license service. • The allowable number of repairs must not have been exceeded. For a successful repair, the message "key has been repaired" is returned. |
-<ack_repair | k> key | Used only with the -repair option when stdin is not available, such as in a remote PowerShell session, to suppress errors about lack of an interactive session. It acknowledges the installation as a genuine copy of the product, that the license is being used in accordance with the EULA, and that the license has not been installed on more machines than the maximum allowed. |
-<validate | t> | Performs a license validation on the connected server name and selected key. |
-<servername | s> servername | Allows connection to a specified server, if specified. If not specified, the servername is assumed to be blank. This parameter is optional. |
-<username | u> | The user name for the server to which you are connecting. If not specified, the username is assumed to be blank. This parameter is optional and not required if a servername is not specified. |
-<password | p> password | The password associated with the user name for the server to which you are connecting. If not specified, the password is assumed to be blank. This parameter is optional and not required if a servername is not specified. |
-<help | h> | Displays information about the options and parameters. |
No option or wrong option | Displays information about the options and parameters. |
See CLI Tasks for the tasks pertaining to the CLI.
License Administration Tasks
These topics explain the tasks that you can perform for license administration, mostly involving use of License Administrator. Some tasks, such as telephone authorization, are accomplished by other means.
License Administrator
GUI Tasks
CLI Tasks
Alternative Authorization Tasks
Notification Viewer
GUI Tasks
To Start License Administrator from Zen Control Center
1. In ZenCC, select Tools > License Administrator.
License Administrator accesses the selected server to determine the type of license required.
If you are not logged in to the server, a dialog appears to log in to the operating system (not the database engine).
Log in with a user name that has administrative privileges on the operating system where the database engine is running. Once logged in, the server name appears in the License Administrator title bar and in the Server Name field.
Note: For servers running a previous version of Zen, use the license tool provided with that version of the product.
If the server is not the one you want, select a different server as described in To Select a Server for License Administration.
To Start License Administrator as a Stand-alone Application
1. Access License Administrator from the operating system Start menu or Apps screen.
This step assumes that License Administrator was installed as part of a Zen default installation. A vendor application that uses an embedded database engine may require that you start License Administrator with different menu commands. The GUI executable is named guilcadm.exe.
The tool connects to the local server on which the database engine is running.
If the server is not the one you want, select a different server as described in To Select a Server for License Administration.
To Select a Server for License Administration
The database engine must be running on the computer you specify so that License Administrator can connect to the engine.
1. In the Server Name field, type the name of the server for which you want to administer database licenses.
As an alternative to typing a server name, you may click Browse to display a list of network servers from which to select. Click the server for which you want to administer database licenses, then click OK.
2. Click Connect (or press Enter).
License Administrator accesses the specified server to determine the type of license required.
• If you are not logged in to the server, a dialog appears to log in to the operating system (not the database engine).
On the login dialog, type the name of an operating system user for User Name. The user must have administrative privileges for the database engine. For Password, type the appropriate password for the user name you specified. Click Login. The server name appears in the License Administrator title bar and in the Server Name field.
Note: For servers running a previous version of Zen, use the license tool provided with that version of the product.
To Authorize a Key
Note that the GUI License Administrator can be used for online authorization of a local machine connected to the Internet, and for remote authorization of the database engine on a machine not connected to the Internet.
1. Ensure that the server name in the title bar is the server for which you want to authorize a database engine key. If not, select a different server as described in To Select a Server for License Administration.
2. Enter the key in the Key field.
Lowercase letters are automatically converted to uppercase.
3. Press Enter or click the button to authorize the key.
The Key field is cleared if the key is successfully authorized.
4. Verify the new license information that appears in the License Information list. (If necessary, press F5 to refresh the list.)
The license is now active. You do not have to restart the database engine.
Note: When authorizing an increase key for user count, session count, or data in use, a permanent license must already exist. The vendor ID of the increase key must match the vendor ID of the permanent key.
Tip... Product authorization is tied to your machine's hardware configuration. After you have authorized a product key on a machine, changes to certain hardware configuration items could disable the key. If you need to change hardware configuration, deauthorize the key first. Deauthorizing the key disassociates the product key from the unique hardware configuration. After you complete the hardware configuration changes, you can again authorize the product key.
To Display Remaining Authorizations
1. Ensure that the server name in the title bar is the correct server for this operation. If not, select a different server as described in To Select a Server for License Administration.
2. Click Remaining Authorizations.
The number of remaining authorizations displays for all product keys.
To Hide Expired Licenses
1. Ensure that the server name in the title bar is the server for which you want to hide expired licenses. If not, select a different server as described in To Select a Server for License Administration.
2. Click Hide Expired, if it is not already selected.
The list of licenses changes to exclude all expired licenses.
Note: The Hide Expired checkbox is selected by default and can be selected or cleared as needed.
To Deauthorize a Key
Note: Temporary licenses cannot be deauthorized. They expire at the end of their evaluation period.
1. Ensure that the server name in the title bar is the server from which you want to deauthorize a database license. If not, select a different server as described in To Select a Server for License Administration.
2. Click a Product name in the License Information list.
You can select multiple keys by holding down the Shift or Control keys and clicking the desired product names.
3. Click the button to deauthorize the key.
Note: You cannot deauthorize a key in a failed validation state. Either rectify the issue before deauthorizing or call Zen support for assistance.
Tip... When you deauthorize a product key, all increase keys for user count, session count, or data in use associated with that product key are automatically deauthorized as well.
To Repair a Key
Tip... After you have applied a product key on a machine, changes to the hardware configuration can cause a key to fail validation or become disabled, requiring a repair. To avoid the need for a repair, deauthorize the key before changing the hardware configuration and authorize the key again after the new configuration is complete.
1. Ensure that the server name in the title bar is the server for which you want to repair a key. If not, select a different server as described in To Select a Server for License Administration.
2. In the License Information list, click the Product name of the product with the key you want to repair.
3. Click Repair.
4. In the dialog box that opens, confirm that this is a genuine copy of the software product. When the repair is done, a completion message is displayed.
To Display License Information
1. Ensure that the server name in the title bar is the server for which you want to administer database licenses. If not, select a different server as described in To Select a Server for License Administration.
2. View the information for the authorized licenses in the License Information list.
Note: You must first authorize a key to display information about the associated license, such as user count, session count, data in use, license type, expiration date and so forth. Once authorized, if the license is not what you want, you may deauthorize it provided that the license it is not a temporary one. Temporary licenses expire on their own and cannot be deauthorized.
See To Authorize a Key and To Deauthorize a Key.
See To Authorize a Key and To Deauthorize a Key.
To Determine a Total User Count
1. Ensure that the server name in the title bar is the server for which you want determine a database user count. If not, select a different server as described in To Select a Server for License Administration.
2. For a particular product, total the user count values that appear in the License Information list in the User Count column. Exclude any values for expired temporary licenses.
For example, total all values for the Zen Enterprise Server product for the permanent license, all user count increases, and any temporary licenses that have not expired.
The sum is the total number of users who can concurrently connect to the database engine on the server.
Note: An easier way to determine the total user count is with Monitor. See Monitoring Resource Usage in Advanced Operations Guide. The maximum value for User Count is the total user count for the permanent license, all user count increase licenses, and any temporary licenses that have not expired.
To Determine the Session Count Limit
1. Ensure that the server name in the title bar is the server for which you want determine a session count limit. If not, select a different server as described in To Select a Server for License Administration.
2. For a particular product, total the session count values that appear in the License Information list in the Session Count column. Exclude any values for expired temporary licenses.
For example, total all values for the permanent license, all session count increases, and any temporary licenses that have not expired. The sum is the total number of sessions that can concurrently connect to the database engine on the server for that particular product (the session count limit).
Note: An easier way to determine the session count limit is with Monitor. See Monitoring Resource Usage in Advanced Operations Guide. The maximum value for Session Count is the session count limit for the permanent license, all session count increase licenses, and any temporary licenses that have not expired.
To Determine the Data in Use Limit
1. Ensure that the server name in the title bar is the server for which you want to determine a data in use limit. If not, select a different server as described in To Select a Server for License Administration.
2. For a particular product, total the data in use values that appear in the License Information list in the Data In Use GB column. Exclude any values for expired temporary licenses.
For example, total all values for the permanent license, all data in use increases, and any temporary licenses that have not expired. The sum is the maximum permitted amount in gigabytes for all concurrently open data files for that particular product.
Note: An easier way to determine the data in use limit is with Monitor. See Monitoring Resource Usage in Advanced Operations Guide. The maximum value for Data in Use MB is the data in use limit for the permanent license, all data in use increase licenses, and any temporary licenses that have not expired.
Be aware that License Administrator uses gigabytes (GB) for units because that is how data in use is associated with a key. Monitor uses megabytes (MB) as the units for resource usage and kilobytes (KB) for file size. The different contexts require units appropriate for each context.
Be aware that License Administrator uses gigabytes (GB) for units because that is how data in use is associated with a key. Monitor uses megabytes (MB) as the units for resource usage and kilobytes (KB) for file size. The different contexts require units appropriate for each context.
To Refresh the License Information List
1. Ensure that the server name in the title bar is the server you want. If not, select a different server as described in To Select a Server for License Administration.
2. Press the F5 key.
The information for applied licenses is redisplayed, and information is cleared from the Key field.
The Server Name field is cleared then displays the machine name to which License Administrator is currently connected. For example, suppose License Administrator is connected to ZEN1 and you attempt to connect to ZEN2, which does not have a database engine running. License Administrator displays a message that it could not connect, and ZEN2 is displayed in the Server Name field. After you press the F5 key, Zen1 is displayed in the field.
To Display Help
1. Click Help from the menu bar of the License Administrator. The License Administrator Graphical User Interface section opens. It enables you to identify and understand the purpose of the objects on the GUI.
2. To consult other areas of documentation about the License Administrator, access the Table of Contents for the documentation and click the desired area:
• License Administration Concepts — To understand the basics of License Administrator
• License Administrator Command Line Interface — To understand the options and parameters for the CLI
• License Administration Tasks — to Perform activities with License Administrator.
CLI Tasks
Note: All of the following tasks use the 32-bit clilcadm command. On 64-bit Windows systems, the name is w64clilcadm. On 64-bit Linux and macOS systems, it is clilcadm64, but clilcadm also works because it calls clilcadm64.
To Display Information about a Key
1. To display information about all keys, enter the following command:
clilcadm -i
2. To display information about a specific key, enter the following command:
clilcadm -i key
See CLI Syntax for the columnar information returned by the -i option.
To Perform a Validation
1. To perform a validation, enter the following command:
clilcadm -t
Tip... To determine the product key postvalidation state and date, use the -i option to display information about the specific key.
To Display Remaining Authorizations
1. To display the remaining authorizations for all product keys, enter the following command:
clilcadm -n
2. To display the remaining authorizations for a specific key, enter the following command:
clilcadm -n key
Tip... To determine a product key, use the -i option to display information about all keys. See To Display Information about a Key.
To Authorize a Key
1. Enter the following command:
clilcadm -a key
Tip... When you authorize an increase key for user count, session count, or data in use, a permanent product key must already exist. The vendor ID of the increase key must match the vendor ID of the permanent key.
To Deauthorize a Key
1. Enter the following command:
clilcadm -d key
Tip... When you deauthorize a product key, all increase keys for user count, session count, or data in use associated with that product key are automatically deauthorized as well.
To Remove Keys Without Deauthorizing
Sometimes you may need to remove a key and its associated increase keys for user count, session count, or data in use without deauthorizing the product. This action is called "clearing" a key.
1. To clear a specific key, enter the following command, where key is the individual key you want to clear:
clilcadm -c key
2. To clear all keys, enter the following command:
clilcadm -c
With either command, you can include the "force" parameter if you want to suppress the clear confirmation message.
Example: clilcadm -c force
To Repair a Key
1. Enter the following command:
clilcadm -e key
2. The command window displays a message asking you to confirm that this is a genuine copy of the software product. Enter "A" to confirm. After the repair is complete, the command window displays a message confirming the repair.
Note: In environments that do not support stdin, such as remote PowerShell sessions, you must add the -ack_repair or -k option to suppress errors about lack of an interactive session.
To Display Help
1. Enter either of the following commands:
clilcadm -<help | h>
clilcadm ?
Alternative Authorization Tasks
Zen provides some alternate ways to authorize and deauthorize your Zen product. If possible, however, authorize Zen using online authorization. If the machine where Zen is installed has only remote internet access, you can authorize remotely.
Tip... See To Authorize a Key for information on online authorization.
To Authorize a Key Remotely
Note that the GUI License Administrator can also be used for remote authorization if you connect to a remote database engine.
1. At a command prompt, enter the following command:
clilcadm -a key -<server|s> servername -<username|u> username -<password|p> password
If the machine where Zen is installed does not have internet access, offline authorization is available.
To Deauthorize a Key Remotely
1. At a command prompt, enter the following command:
clilcadm -d key -<server|s> servername -<username|u> username -<password|p> password
Tip... When you deauthorize a product key, all increase keys (user count, session key, or data in use) associated with that product key are automatically deauthorized as well.
To Authorize a Key Offline
Only consider offline authorization if the machine on which you are running Zen does not have internet access. Offline authorization involves three tasks using two machines. For example, machine A needs to authorize the Zen product but has no Internet connectivity. Machine B has no Zen installation but has Internet connectivity.
Task 1 - Generate Authorization Request Data
1. On machine A, enter the following at a command prompt:
clilcadm -<generate|g> product_key output_filename.ath
2. Save the file to a portable storage device or in a location that can be easily accessed by the machine that has Internet connectivity.
Tip... If the machine with Internet connectivity does not have Zen installed, you must also copy the licgetauth.exe file from the Zen \bin folder to the portable storage device or remote location.
Task 2 - Transmit Authorization Request Data and Retrieve Authorization Key Data
1. On machine B, connect to the portable storage device or access the location where you saved the Authorization Request Data file.
2. Enter the following at a command prompt, where output_filename.ath is the file you created in step 1 of task 1:
licgetauth.exe output_filename.ath
The above command retrieves the Authorization Key Data used to authorize the key and the product. The authorization key data is saved as a .pky file to the same location where you saved the authorization request file.
Tip... If you saved the Authorization Request Data and Authorization Key Data files to a hard drive, you will need to copy these files to either a portable storage device or a remote location.
Task 3 - Install Authorization Key Data
1. Back at machine A, connect once more to the portable storage device or access the location where the authorization key data was saved.
2. Enter the following at a command prompt, where authorization_filename.pky is the file created in step 2 of task 2:
clilcadm -a authorization_filename.pky
Zen is now authorized.
To Deauthorize a Key Offline
Deauthorizing a key offline requires that you contact Actian technical support.
Telephone Authorization
In the event that it is not possible to authorize keys online, remotely, or offline, you can authorize Zen Enterprise Server, Cloud Server, or Workgroup using telephone authorization.
Telephone authorization requires that you have completed a successful installation and have a valid product key. If you do not have a product key, you can obtain one from Actian Corporation or your software vendor. Telephone authorization is available by calling 1.800.287.4383 toll-free in the United States or 00800.1212.3434 toll-free in Europe.
To authorize a key by telephone, you can use the Phone Authorization Wizard or the command line tool. The Phone Authorization Wizard is a GUI application available on Windows, Linux, and macOS. The command line tool clipaadm works on all supported platforms. Both methods guide you through the same authorization steps.
To Authorize a Key Using the GUI Phone Authorization Wizard
1. Be sure that you have completed a successful installation of Zen Enterprise Server, Cloud Server, or Workgroup and a have a valid product key.
2. At a command prompt on the system where the engine is installed, enter guipaadm.
3. In the wizard that opens, follow the steps provided.
To Authorize a Key Using the Command Line Phone Authorization Tool
The steps to authorize a key by phone from a command prompt are provided under clipaadm.
Telephone Deauthorization
Telephone deauthorization is not available. If you authorized your license using telephone authorization, you must contact Actian Corporation to deauthorize it.
Notification Viewer
Notification Viewer is a tool for displaying messages logged by the licensing components. The purpose of the tool is to inform you of noteworthy licensing messages in a noticeable but unobtrusive manner. Although not part of License Administrator, Notification Viewer is mentioned here because of its usefulness in working with licenses.
To View Licensing Messages in Logging Repositories
See the following topics in Advanced Operations Guide:
Last modified date: 10/31/2023